Month: November 2018
-
Monthly notes 35
December is just around the corner but before that here’s monthly notes for November. More about leadership and stories, something about software development. Issue 35, 13.11.2018 Frontend CSS and Network Performance What are best network performance practices when it comes to loading CSS? How can we get to Start Render most quickly?… Jatka lukemista →
-
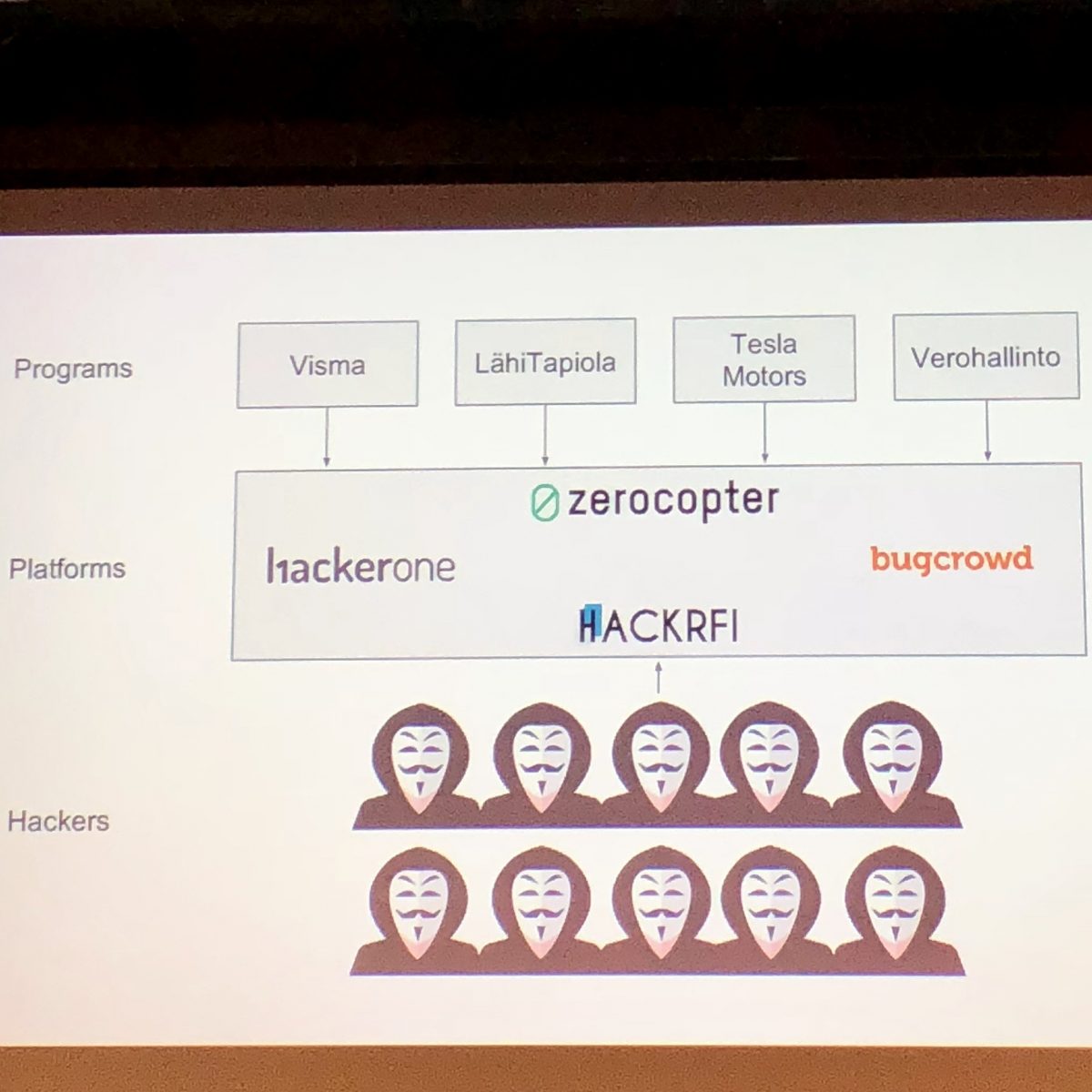
Notes from OWASP Helsinki chapter meeting 35: Bug Bounty programs
Have you ever wondered how to become a bug bounty hunter or wanted to organize a bug bounty program? OWASP Helsinki chapter meeting number 35 told all about bug bounty programs from hacker and organizer point of views. The event was held 6.11.2018 at Second Nature Security (2NS) premises in Keilaniemi.… Jatka lukemista →