Tag: owasp
-
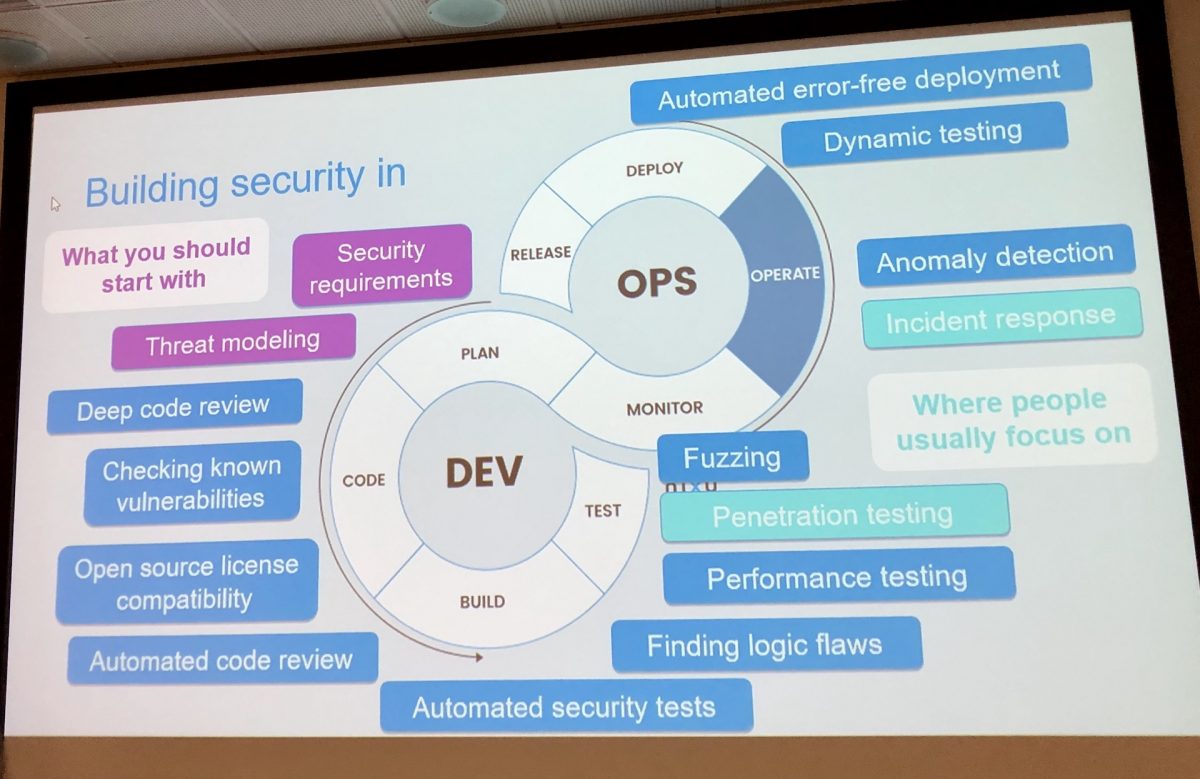
Notes from OWASP Helsinki chapter meeting 36
OWASP Helsinki chapter meeting number 36 was held 12.2.2019 at Veikkaus premises in Pohjois-Haaga. The theme for this meeting was about software security and the topic was covered with two talks and with a card game. Here’s my short notes. What Every Developer and Tester Should Know About Software Security The event started with “What Every…
-
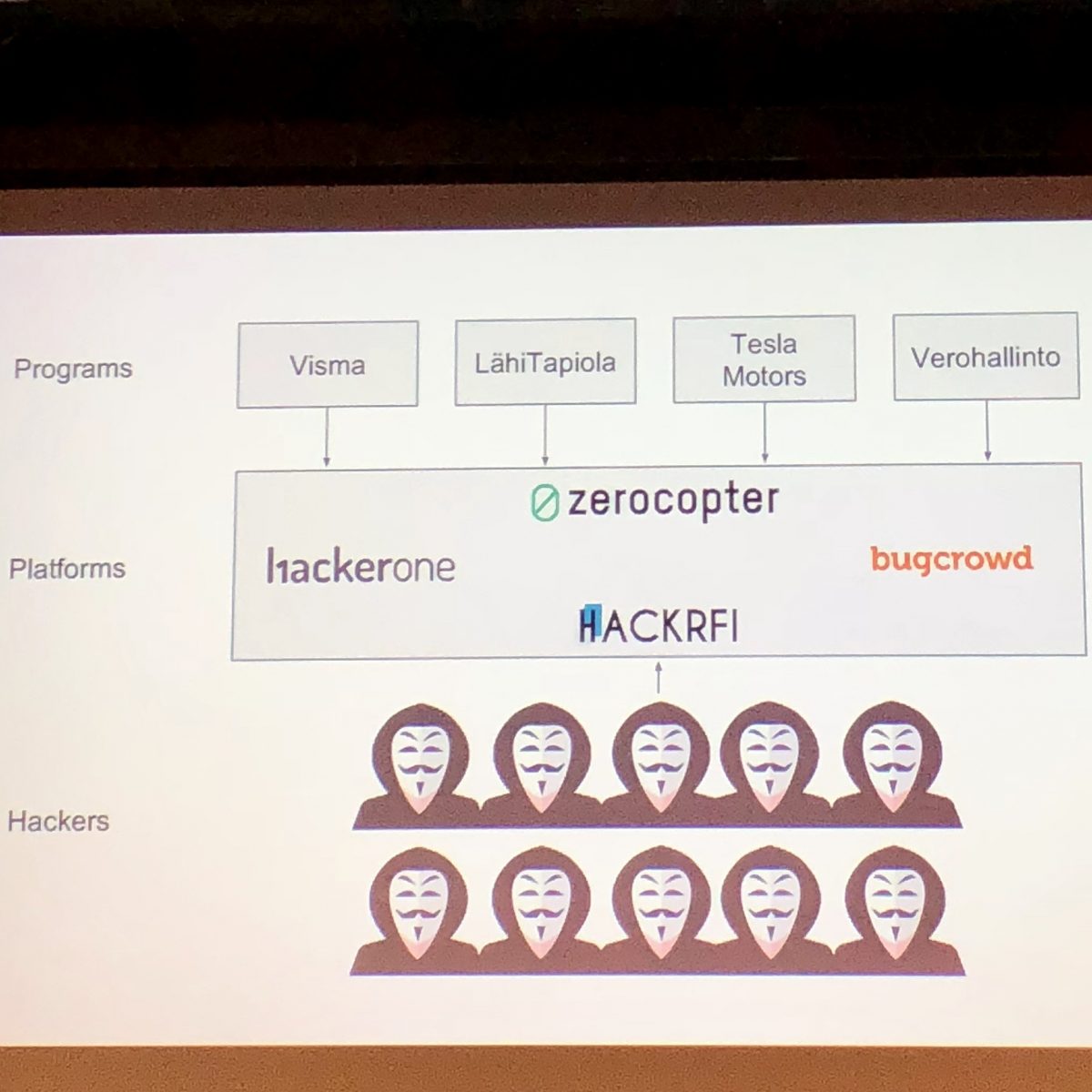
Notes from OWASP Helsinki chapter meeting 35: Bug Bounty programs
Have you ever wondered how to become a bug bounty hunter or wanted to organize a bug bounty program? OWASP Helsinki chapter meeting number 35 told all about bug bounty programs from hacker and organizer point of views. The event was held 6.11.2018 at Second Nature Security (2NS) premises in Keilaniemi.… Jatka lukemista →
-

OWASP Helsinki chapter meeting 34: Secure API
OWASP Helsinki Chapter held a meeting number 34 last week at Eficode with topics of “Perfectly secure API” and “Best friends: API security & API management”. The event gave good overview to the topics covered and was quite packed with people. Eficode’s premises were modern and there was snacks and beverages.… Jatka lukemista →
-

Notes from Owasp Helsinki Chapter Meeting 27
Security is important part of software development and often it doesn’t get enough attention or developers don’t know enough about it. I have been following Troy Hunt on Twitter for some time and as he was coming to Owasp Helsinki Chapter Meeting #27 it was great opportunity to hear about application security at first hand.……