Have you ever wondered how to become a bug bounty hunter or wanted to organize a bug bounty program? OWASP Helsinki chapter meeting number 35 told all about bug bounty programs from hacker and organizer point of views. The event was held 6.11.2018 at Second Nature Security (2NS) premises in Keilaniemi. Here’s my short notes.
Notes from OWASP Helsinki chapter meeting #35
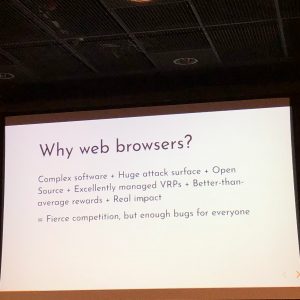
“Hunting for bounties in a web browser” by Juho Nurminen from 2NS started the event talks and told about how to approach the issue and showed some findings in details. For the usual of understanding the technology and focusing on what you know, it’s beneficial to read up prior art. Is it repeatable bug? Reproduce it in other context. The talk presented cve-2018-6033 (extension code can execute downloaded files), cve-2018-6039 (XSS in DevTools, privileged API can be overwritten) and cve-2011-2800 (data leak across origins). tl;dr; pwn things, submit crbug.com, profit.
“#OWASPHelsinki 35 started by @jupenur hunting bounties in web browsers. Understand the tech (web, js, extensions, plugin API, devtools, NaCI, WebAssembly, etc.). Focus on what you know. Read up prior art. Nice examples of bugs found. @OWASPHelsinki meetup hosted by @2NS_fi.” – @walokra
In “How to become a bug bounty hunter” Iiro Uusitalo from Solita talked about bug bounty platforms and tips to be succesful. In short: POC or GTFO, recon, stay on scope, automate all the things, focus, report, wait, profit, join the community.
“How to become a bug bounty hunter, told by @iiuusit at @OWASPHelsinki meetup. Tips: poc or gtfo, recon, stay on scope, automate all the things, focus, report, wait, profit, join the community. #OWASPHelsinki” – @walokra
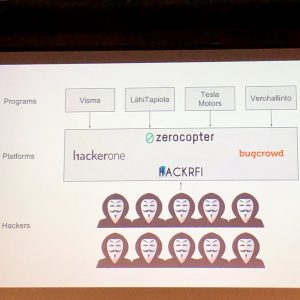
“Running a successful bug bounty program” by Thomas Malmberg from Hackrfi bug bounty program covered the topic from the “random dude from the other side of the table” point of view. “What really matters is finding bugs” but there’s a lot of things to manage. It comes to managing expectations of hackers and program owners. And remembering that hackers work for you (program owners) but they are not your employees.

“What really matters is finding bugs.” @tsmalmbe from @hackrfi told how to run a successful bug bounty program at @OWASPHelsinki meetup. Managing expectations of hackers and program owners. Remember: hackers work for you; hackers are not your employees. #OWASPHelsinki” – @walokra
The evening ended with a panel & discussion about bug bounty with Juho, Iiro and Thomas. There was lots of interesting questions asked and here’s some of them in short.
- Hardware bug bounties, how to do if device not publicly available?
- On premises hack days -> not so successful, too little time, concentrate on low hanging fruits.
- Wide scope -> low hanging fruits.
- OWASP Top 10 covers almost everything.
- Everyone is scared of finding remote code execution.
- Business impact findings.
- Recon: who we are, what we do -> what has big business impact. Also where’s the legacy code?
- Always estimate, run some CVSS estimator.
- Use Google’s approach.
- Fairness and trust. Programs task is to create trust.
- Program has rules which covers legal matters. Read the rules, ask.
- Program runner went public, lots of bugs, hackers pwned whole system.
- Communication issues.
- Program runner: call on Friday night, database lost. bug bounty program to blame.
- Not competing.
- You shouldn’t do bug bounty if you don’t have enough security maturity. Too many reports at start (duplicates, cost much, etc.), then nothing if you don’t pay.
- Low hanging fruits are not interesting for good hackers
- Pentesting last 30 days and result is report covering certain things.
- Bug bounty concentrates on specific aspect.
- Threat model for users? Depends on product / service you are providing.
- 0-day on some Finnish site selling on USA black market -> not much interest.
- Pentesting should be done first.
- Educating the bottom of the pyramid. Hammer and nails.
- Public programs generate lots of noice vs. private
- More automated things, scripts to detectivive things, AI
- Bug hunter side: more professional all around the pyramid, more spam




Leave a Reply