The DevOps Conference was held this week and on the Expo there were companies showing their services. One of those was Secure Code Warrior which provides a learning platform for teaching developers the skills they need to produce secure code. Last year I wrote about their bootcamp but now it was time to participate in their “The DEVOPS Secure Coding Tournament!”

The DevOps Conference Secure Coding Tournament
Identifying and fixing vulnerable code is an important skill in software development and there are different ways to enhance your skills. During the The DevOps Conference Secure Code Warrior organized the The DEVOPS Secure Coding Tournament in their learning platform which allowed you to improve your secure coding skills.
“The tournament allows you to compete against the other participants in a series of vulnerable code challenges that ask you to identify a problem, locate insecure code, and fix a vulnerability.”
The challenges were based on the OWASP Top 10 and there were good explanations for the vulnerabilities and solutions to get better understanding of the underlying problems. You get to use your preferred software language such as JavaScript, Java EE / Spring, C#, Go, Ruby on Rails, Python Django & Flask, Scala Play, Node.JS, React, and both iOS and Android development languages.
I chose to use JavaScript and Node.js (Express) as it’s the recent language I’ve used with different libraries and concepts. From previous experience from Secure Coding Bootcamp it helps to know not just the chosen language and framework but also other libraries from the ecosystem. For example with Node.js (Express) there were questions relating to use of Handlebars, LDAP, Mongoose, XML, etc. But most of the challenges were logical to deduce even if you didn’t know e.g. XPath.
The missions were presented as a world map and there was total of 8 levels to compete. The usage of the map and potentical attackers was a bit confusing in my mind but might fascinate some.
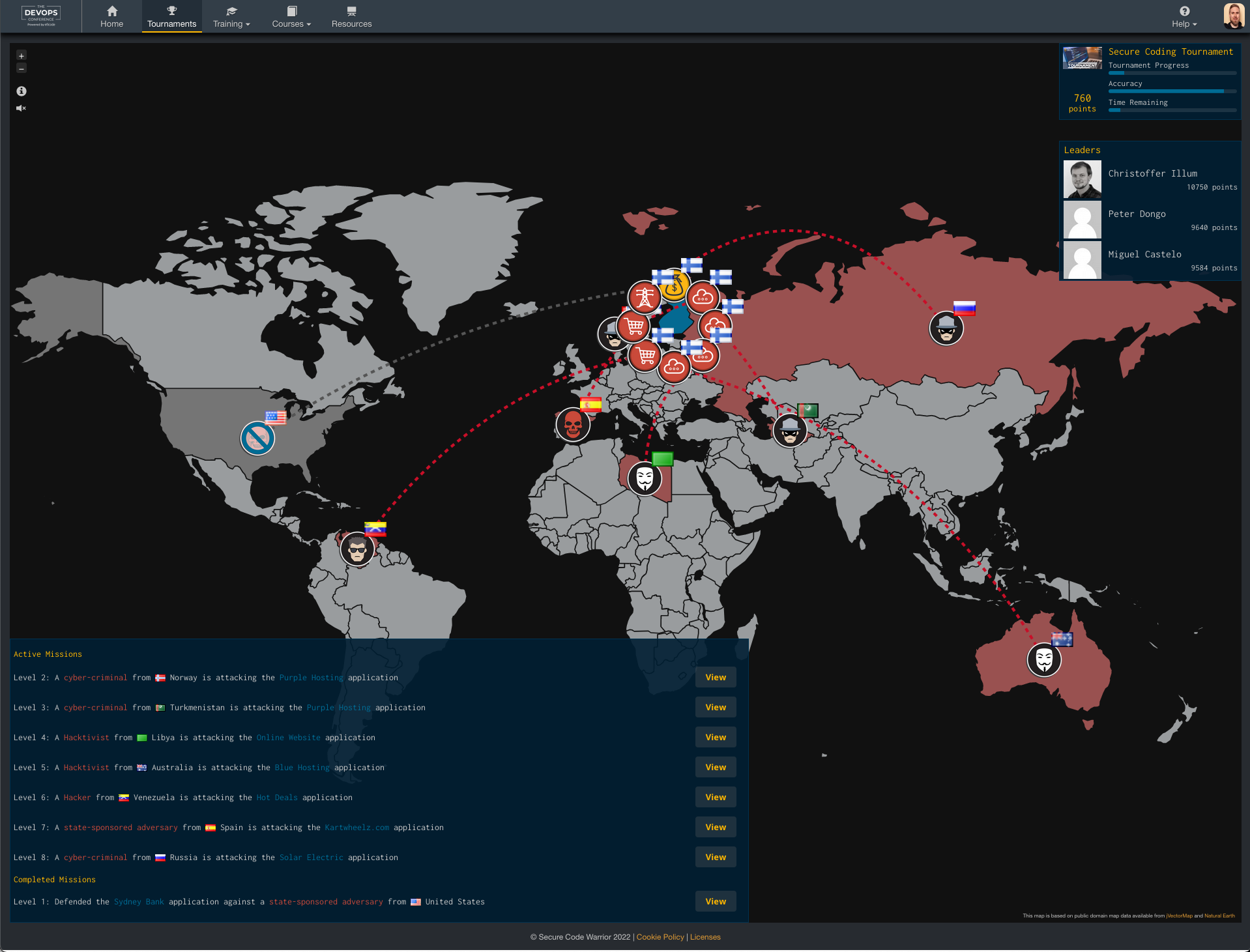
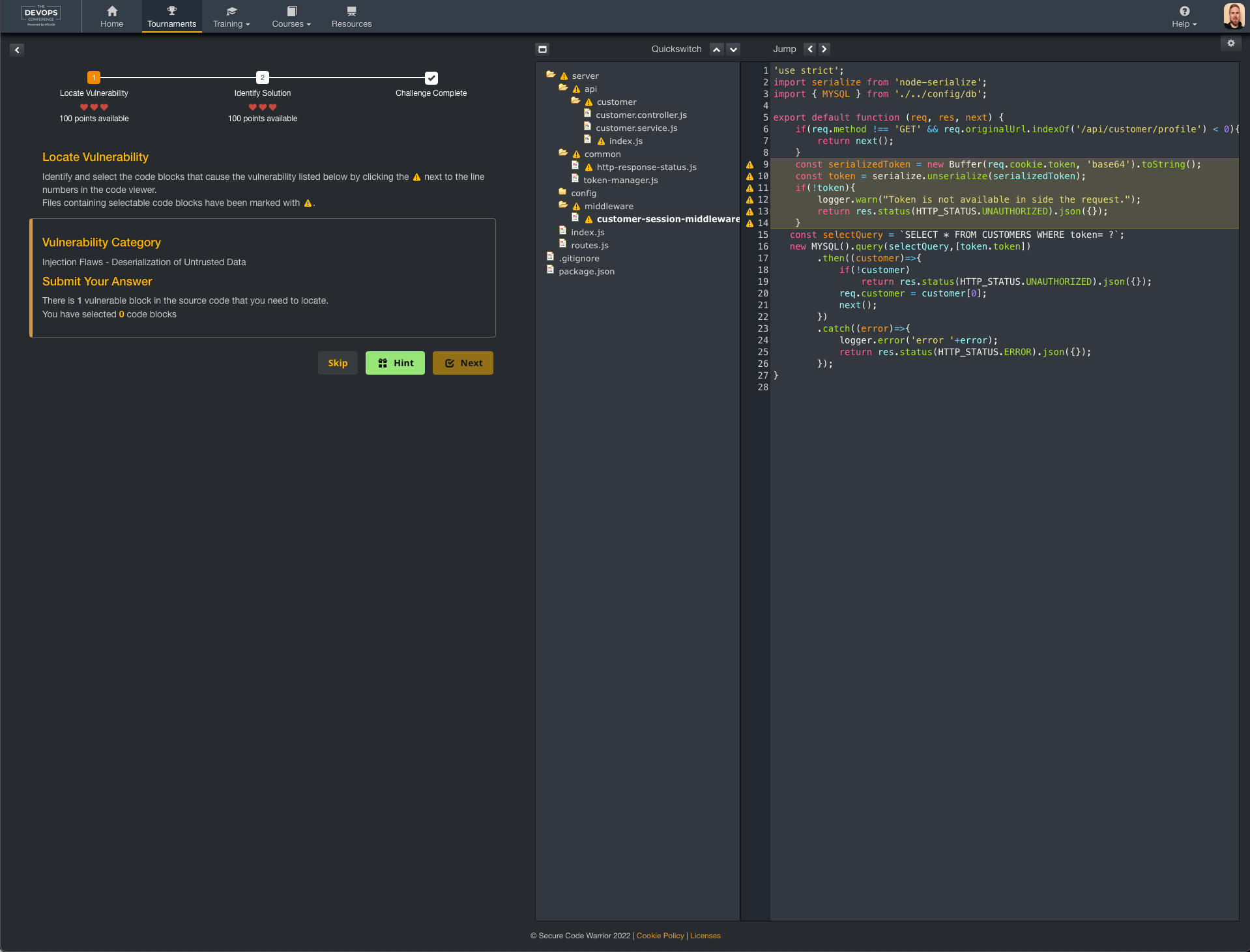
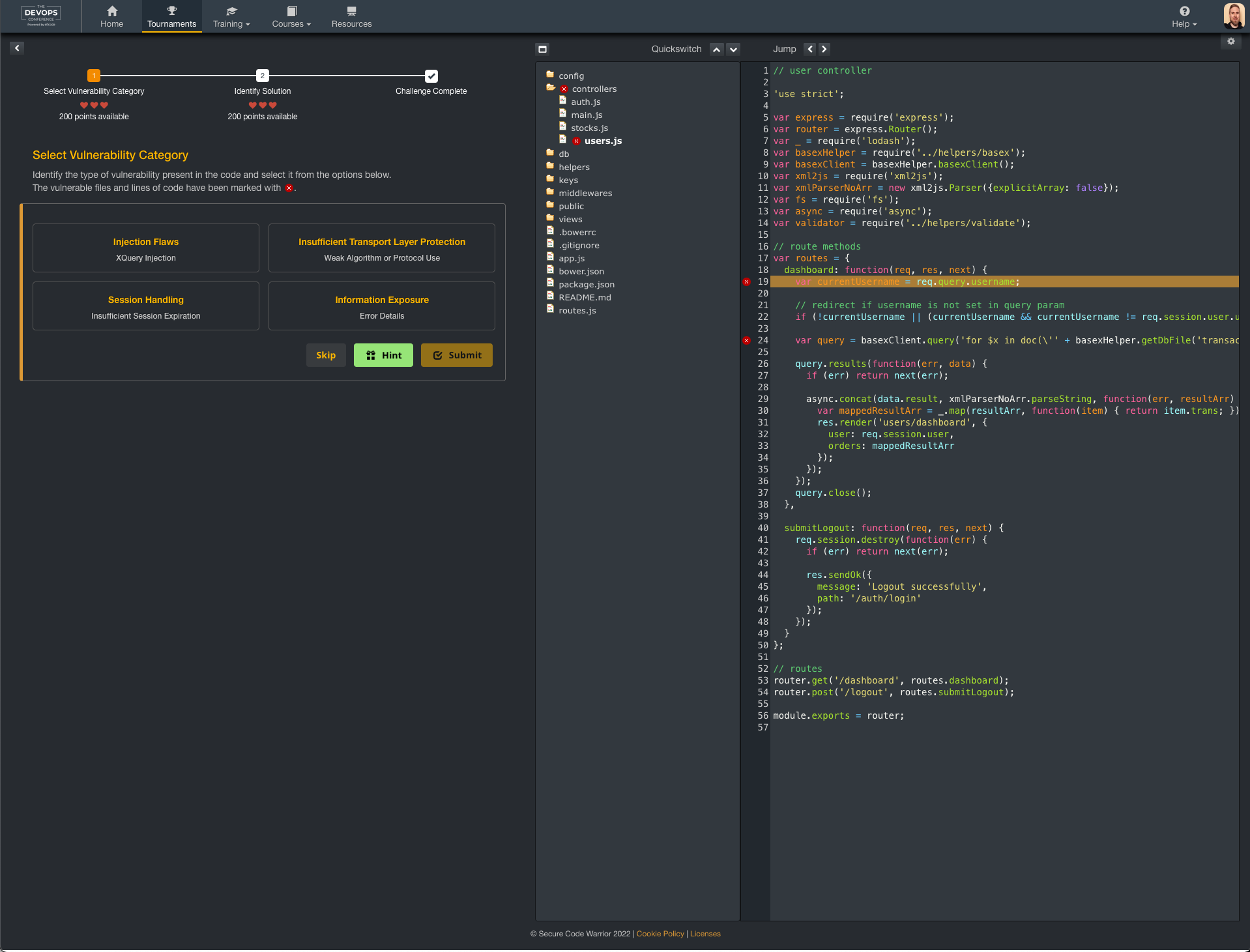
In each one of the mission there were 5 different challenges with locating vulnerability by selecting one or more code rows or identifying what kind of vulnerability was shown. You got 3 lives to get it right. Then you got four possible solutions to identify which would fix the issue.
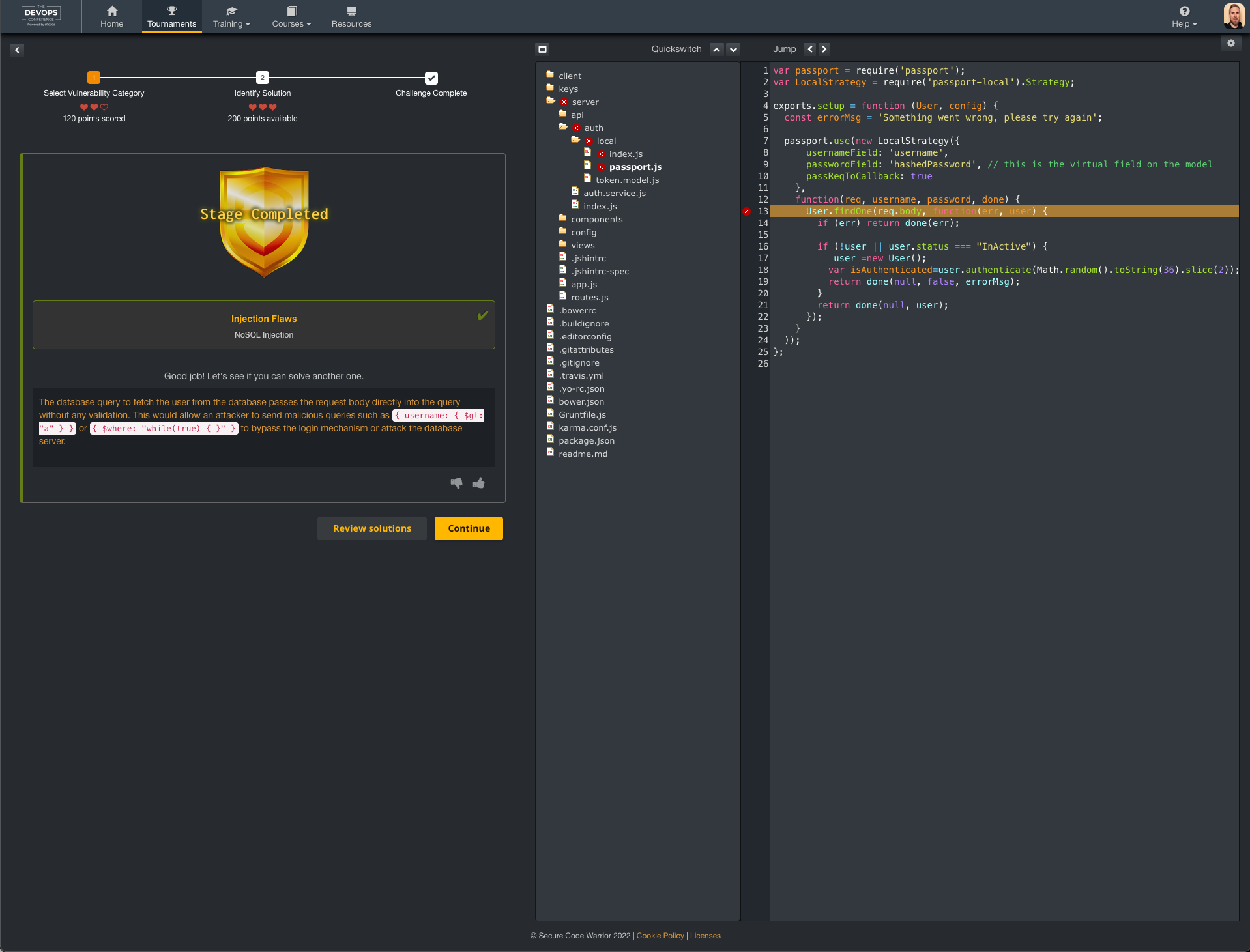
After you either got it right or not, the solution was shown with short explanation to teach you more about it.
Tournament participants had two days to complete the challenges but I noticed the tournament on the last day around four hours before it ended. Fortunately it was said that it should took around two or three hours to complete.
I’ve to admit that at first I wasn’t so sure if I would do more than a few challenges regarding the timeframe for completing all of them but it was actually quite addictive to see how well you could identify the vulnerable parts of the code and what the solutions would be although some of the libraries were not so familiar. And seeing that I did quite well on the leaderboard helped to finish it.
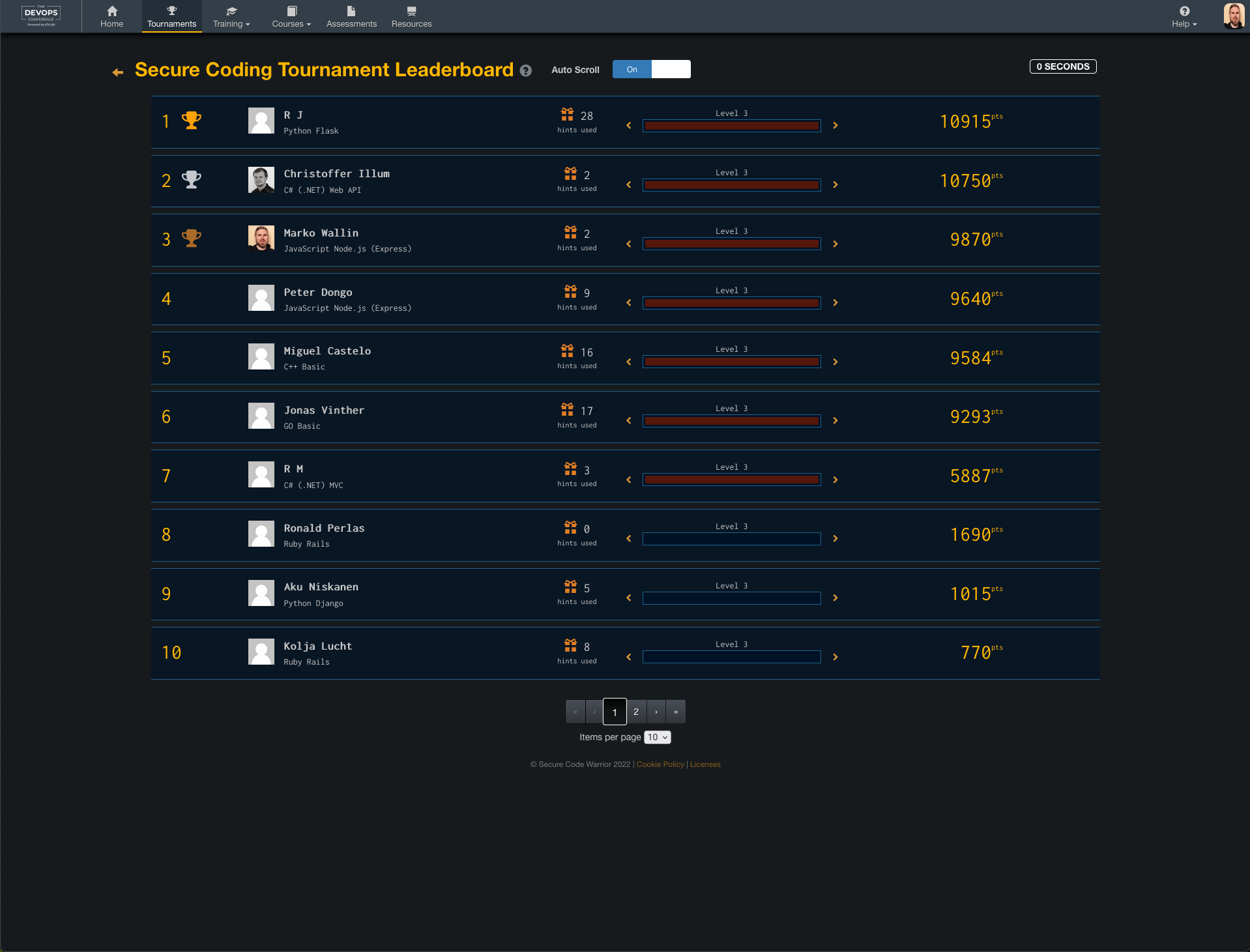
On the leaderboard I managed to gather enough points for the third position and won a Secure Code Warrior T-shirt. Yay! The total points available was 12000 so you could say that there was a lot of points (easily) missed.
The overall experience of the tournament was great and it was fun. There were several challenges which weren’t quite clear if you didn’t know the used library and couple of solutions were tricky as although the solution was “right” the other solution was better (in terms of e.g. better algorithm, etc.).
I’ve now done two Secure Code Warriors’ OWASP Top-10 learning challenges (Bootcamp and this tournament) and can say that although they don’t actually teach you to write secure code, they teach you to read code and identify vulnerable parts. They also have more practical and interactive approaches to build secure coding skills systematically but I haven’t tried those missions.
Leave a Reply