Software development contains many aspects which the developer has to take care and think about. One of them is information security and secure code which affects the product and its users. There are different ways to learn information security and how to create secure and quality code and this time I’ll shortly go through what Secure Code Warrior Secure Code Bootcamp has to offer.
For the record other good resources I’ve come across are Kontras application security training for OWASP Top 10 and OWASP Top 10 API, hands-on approaches like Cyber Security Base MooC, Wargames, Hack the Box and Cybrary.
Secure Code Bootcamp
Kick-start your journey to creating more secure, quality code with Secure Code Bootcamp – our free mobile app for early-career coders.
Secure Code Bootcamp
Secure Code Warrior provides a learning platform for developers to increase their software security skills and guide each coder along their own preferred learning pathway. They have products, solutions and resources to help organization’s development teams to ship quality code and also provide a free mobile app for early-career coder: Secure Code Bootcamp.
Application presents common vulnerabilities from the OWASP Top 10 and you get badges as you progress through each new challenge, unlocking new missions as your progress. It teaches you to identify vulnerable code with first short introductions and explanations for each vulnerability of how they happen and where. Each topic is presented as a mission with briefing and code inspection tasks.
OWASP Top 10 are:
- A1:2017-Injection: Injection flaws, such as SQL, NoSQL, OS, and LDAP injection.
- A2:2017-Broken Authentication: Application functions related to authentication and session management.
- A3:2017-Sensitive Data Exposure: Many web applications and APIs do not properly protect sensitive data, such as financial, healthcare, and PII.
- A4:2017-XML External Entities (XXE): Many older or poorly configured XML processors evaluate external entity references within XML documents.
- A5:2017-Broken Access Control: Restrictions on what authenticated users are allowed to do are often not properly enforced.
- A6:2017-Security Misconfiguration: Security misconfiguration is the most commonly seen issue.
- A7:2017-Cross-Site Scripting XSS: XSS flaws occur whenever an application includes untrusted data in a new web page without proper validation or escaping.
- A8:2017-Insecure Deserialization: Insecure deserialization often leads to remote code execution.
- A9:2017-Using Components with Known Vulnerabilities: Components, such as libraries, frameworks, and other software modules, run with the same privileges as the application.
- A10:2017-Insufficient Logging & Monitoring: Insufficient logging and monitoring, coupled with missing or ineffective integration with incident response.
The Secure Code Bootcamp covers 8 of the Top 10 list as the last two are more or less difficult to present in this gamified context, I think.
Play video or read text 
Briefing for code review
Mission briefing contains couple of minute theory lesson of the given vulnerability and teaches you what, where and how to prevent it.

When? 
How to prevent?
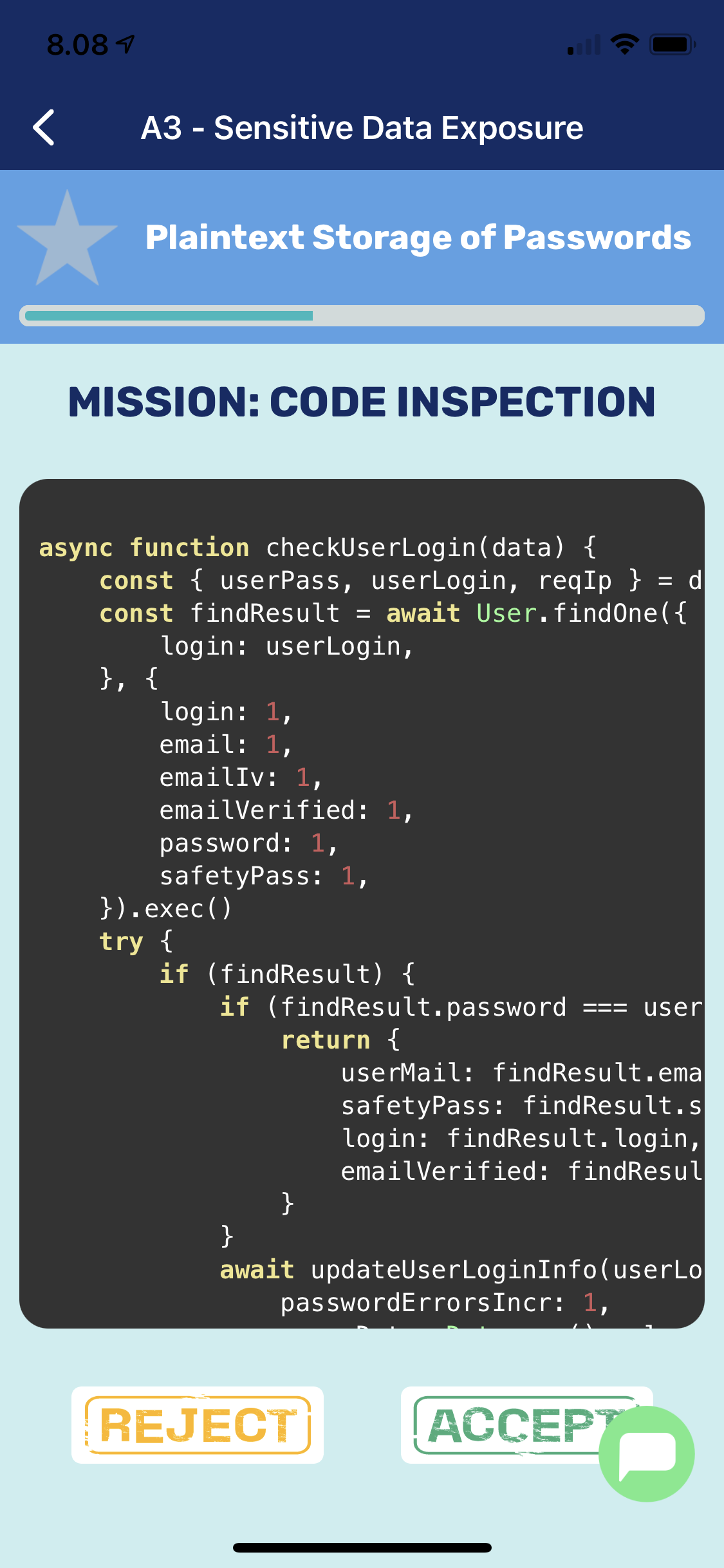
After briefing you’re challenged with code examples in the language you’ve chosen (Node.JS, Python:Django, Java:Spring, C# .NET: MVC). You practically swipe your way through code reviews by accepting or rejecting them. Reading code on mobile device screen isn’t optimal but suffices for the given task. Works better for Node.js than for Java Spring.
Code inspection isn’t always as easy as you would think even if you know what to look for. After succesfully inspected couple of codes you’re awarded with a badge. The briefing tells you what to look for in the code but sometimes it’s a guess what is asked for. The code inspection requires sometimes knowledge of the used framework and inspection is done without context for the usage. Almost every inspection I got 1 wrong which gave me 75% accuracy.
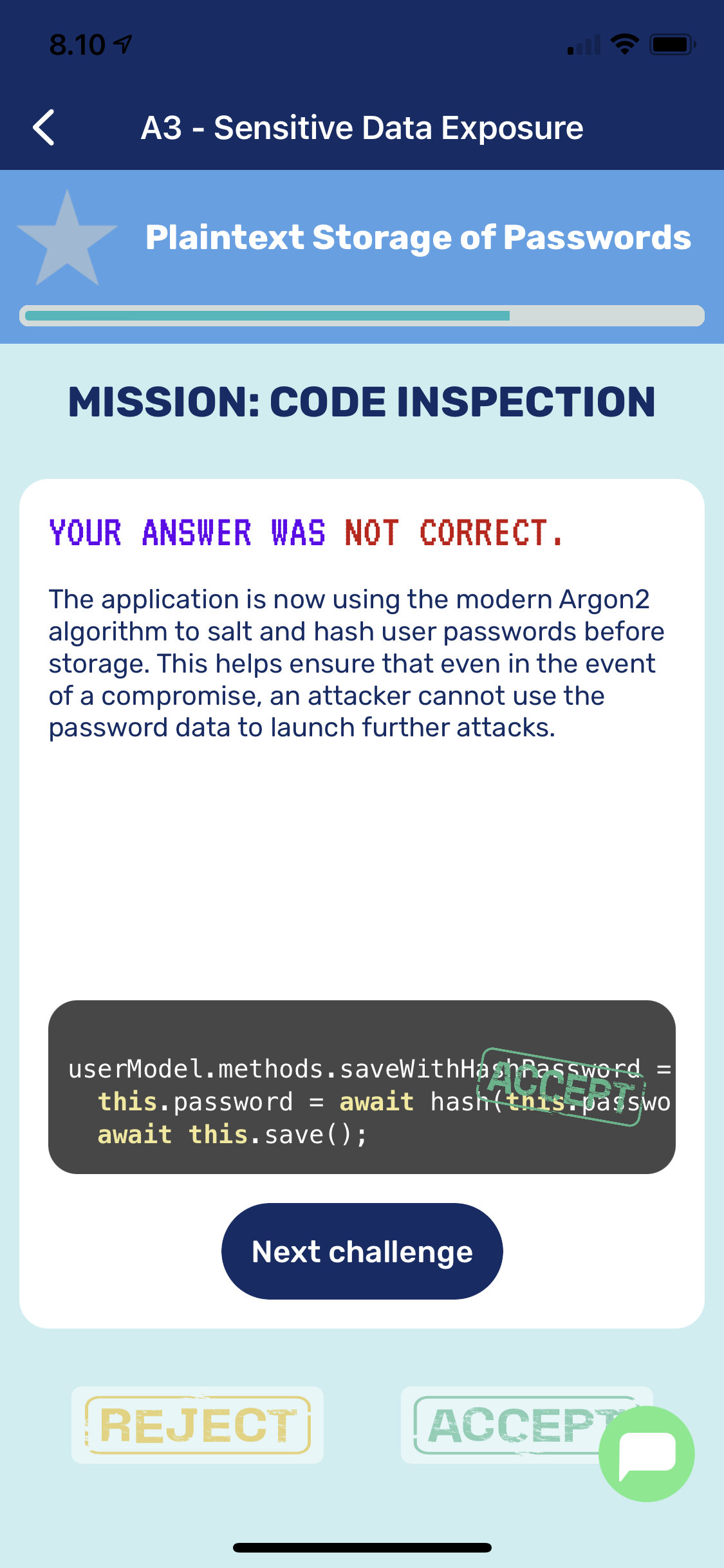
Accept or reject 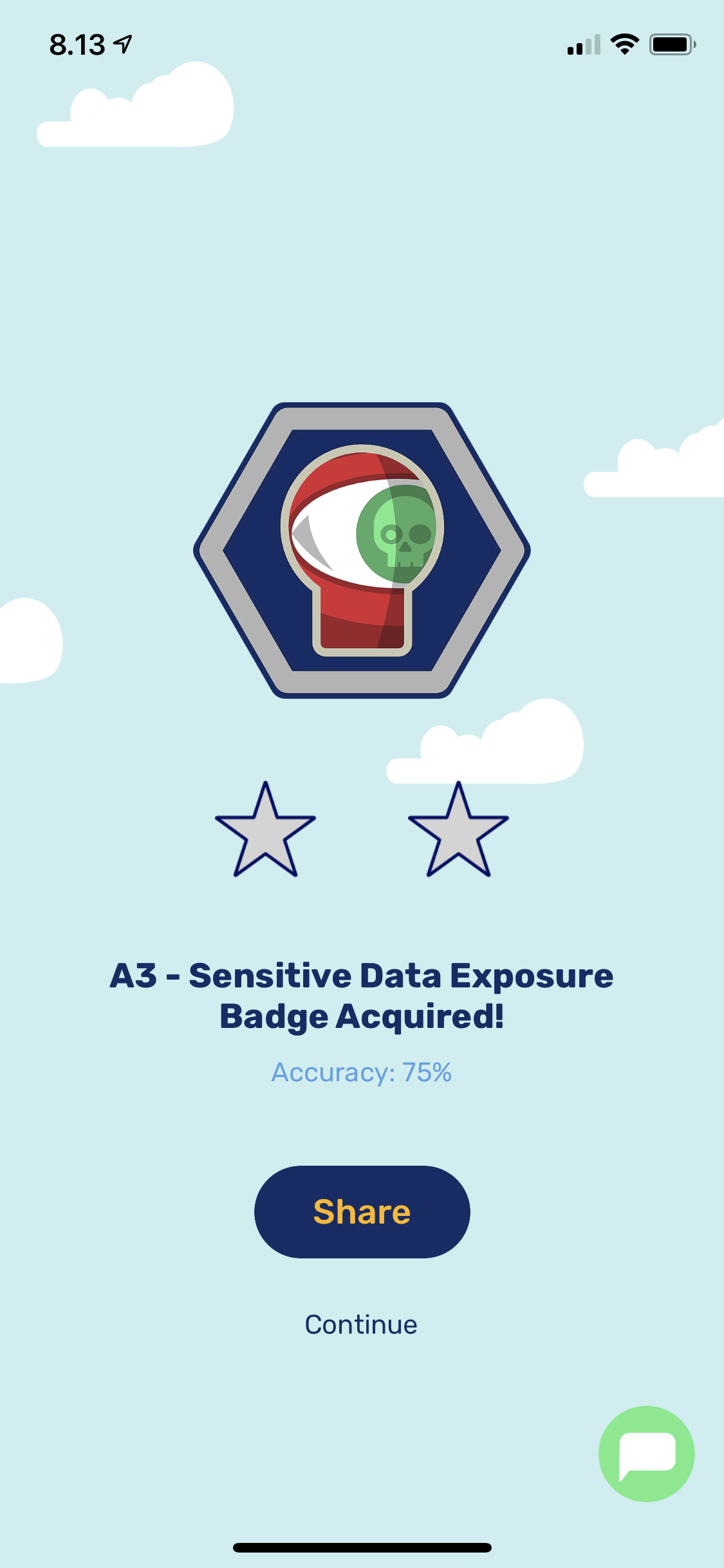
You get a badge
Summary
The approach to teaching security topics this way works ok if you’re code oriented. You’ll learn the OWASP Top 10 in practice by short theory lessons with pointers to how to prevent them and test your code inspection skills for noticing vulnerable aspects of code fragments. Having swiped through the bootcamp the code inspection parts were not always so useful.
The marketing text says “progress along multiple missions and build secure coding skills.” and “Graduate with fundamental secure coding skills for your next step as a coder.” and that is in my opionion a bit much to say. The bootcamp teaches the basic concepts of vulnerabilities and how they look on code but doesn’t teach you to code securily.
In overall the Secure Code Bootcamp for OWASP Top 10 vulnerabilities is a good start for learning what, where, how and why vulnerabilities exists and learn to identify them. You can do the bootcamp with different languages available so replayability value is good.



Leave a Reply